Chrome & Firefox Updated Security Alerts for HTTP Pages
January 16, 2017How Chrome & Firefox Will Change the Treatment of HTTP Pages that Collect Passwords
In January of this year, (2017) Chrome & Firefox will begin showing ‘non-secure’ symbols in the address bar of HTTP pages that request that include a user login. Chrome will also add the notation on pages that capture credit card information; a warning that is already in place in the most recent version of Firefox. While these changes will not have a direct impact on search engine rankings (mobile or otherwise), they could have a significant indirect impact on secondary SEO signals like site engagement, bounce rate, and time on site. They could even hurt Pageviews-per Visit and site conversions, if the impact on the site is widespread.
Historically security notifications have focused only on pages that collect credit card information, so this increased focus on pages that collect login information is relatively new ground. Only about 25% of the web has made the transition to HTTPS so that leaves many HTTP pages potentially affected; especially if they have site-wide login functionality in the page templates. Google has been strongly recommending sites move to HTTPS for over a year, and even created a slight algorithmic ranking boost for sites that do, to incentivise the change. This round of browser updates puts a finer point on the need for websites to update, so that they can continue to build trust and safely engage with their users.
What to Expect
Chrome 56 HTTPS Updates
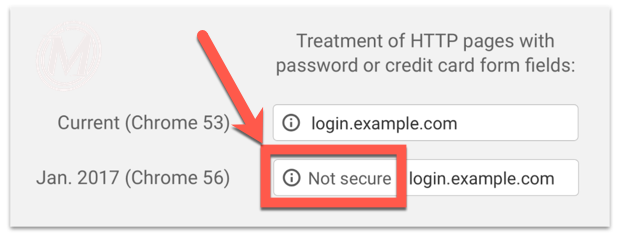
The current desktop Chrome browser is Chrome 55, so the version that will launch later this month is Chrome 56. Chrome is set to auto update by default and it actively checks for updates from Google every 5 hours, so you can expect most visitors to be running Chrome 56 shortly after it launches. Chrome 56 will add a gray “Not Secure” message in the address bar, ahead of the url on all HTTP pages that include login functionality, as shown below: (Google publishes all Chrome updates logs if you need further details.)
*Source: https://blog.chromium.org/2016/09/moving-towards-more-secure-web.html
This is the first step in Chrome’s multi-phased plan to alert visitors to potential security concerns and encourage webmasters to move to HTTPS. The next phases for this project includes the following steps: (Or check out the full announcement from Google, if you prefer.)
- Initially, Chrome will add gray a “Not Secure” message on HTTP pages collecting credit card info or login information (username and passwords) as shown above.
- Then Chrome will add gray “Not Secure” message on all HTTP pages a user accesses when browsing in incognito mode.
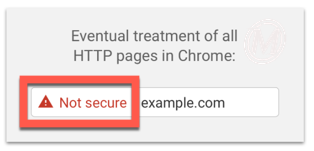
- Eventually, all HTTP pages will show the gray “Not Secure” message.
- Finally, the alert will display in a more aggressive red yield sign and font, instead of just gray text, as illustrated below:
Google hasn’t given a precise timeline for these changes, but we expect them to roll out fully over the next 1-2 years. These changes may roll-out in future versions or Chrome, but it is more likely that some or all of them will roll out as incremental changes within a version number. EX: Version 56.3 or or 57.3.2. The degree of change associated with the update, (full version update or incremental update), may impact the level of information and advanced warning that Chrome makes available before each phase of the plan goes live.
*Source: https://blog.chromium.org/2016/09/moving-towards-more-secure-web.html
Firefox 51 HTTPS Updates
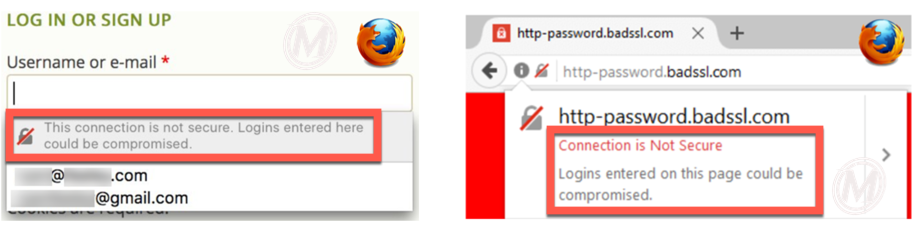
The current version of the Firefox desktop browser is version 50, so the update that will happen this month is to Firefox 51. Firefox is taking more abrupt path to update their HTTP security alerts. Rather than rolling out the updates over time, their update will include a ‘Not Secure’ symbol (a gray lock with a red slash), and an ‘Info’ button in the address bar right from the beginning. They will only be using this treatment for pages that include login information. Firefox’s update does not include pages that only collect credit card information unless they also happen to have a login functionality.
In Firefox, users can expand the ‘Not Secure’ icon to show more detail about why Firefox is displaying the warning for the particular page, and they can also click the ‘Info’ icon to get more general information about HTTPS. Like Chrome, Firefox is also set to auto update by default, so you can expect most users to have the newest version of the browser very soon after it launches.
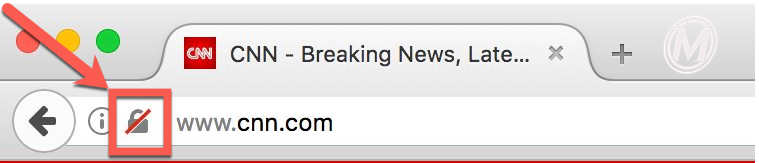
*Source: https://twitter.com/rlbarnes/status/814579588072349697
Firefox will also add an alert for login fields where they serve saved credentials. Like the address bar alert, these in-line form alerts can be expanded for additional information.
**UPDATED JANUARY 25, 2017** Firefox has released details about their changes in a blog January 24, 2017. Full v51 release notes are also public.
Pages That Are At Risk
Below are the four types of HTTP pages that will be affected with these browser updates:
- HTTP pages that collect payment info (warning for Chrome only).
- HTTP pages with dropdown or embedded login information.
- HTTP pages with JavaScript pop-up modals for login or something similar.
- Dedicated login pages that are not on HTTPS.
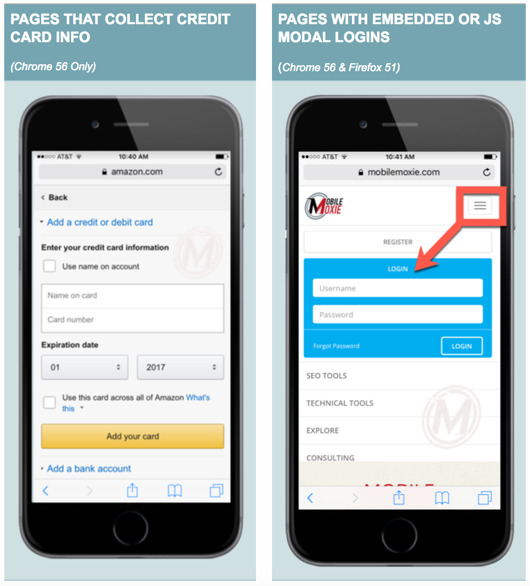
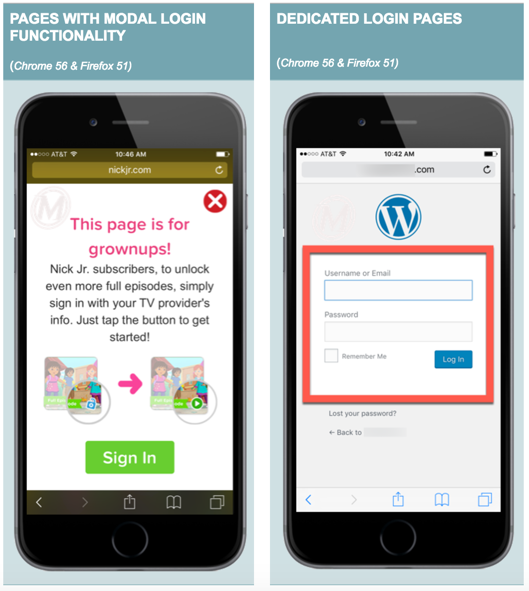
Google has begun rolling out alerts about this browser update in Google Search Console, so be sure to log into Google Search Console and check all protocols of your site including: http://, http://www, https:// and https://www. Search Console counts each of these as separate data sets, and it is possible but unlikely that you could receive the message, even an HTTPS version.
A sample of the Search Console alert is included below. These are generally sent out with sample urls that would be impacted, to help webmasters understand which page templates need to be fixed.
Nonsecure Collection of Passwords will trigger warnings in Chrome 56 for http://www.xyz.com
To: owner of http://www.xyz.com
Beginning in January 2017, Chrome (version 56 and later) will mark pages that collect passwords or credit card details as “Not Secure” unless the pages are served over HTTPS.
Within the message Google will include links to a sample of pages that will be affected but that list shouldn’t be considered comprehensive. You should work within your site to identify and fix all impacted pages.
These Search Console notifications are not being sent out simultaneously, but instead appear to be prioritized by the size of the website, so some sites that will be impacted may still have not received the alert. Just because you didn’t get a message in Search Console it doesn’t mean you won’t be affected. If you’re not sure if your site will be affected, and want to verify before the browser updates go live, you can always download the Chrome 56 Beta to see how it will treat your site(s) when version 56 rolls out. Firefox also offers a beta download for Firefox 51, so you can also use that to test how the new browser will treat to see how Firefox 51 will treat your login pages.
What’s the Fix?
There are a variety of minor work-arounds and fixes, to avoid or minimize the impact that these new security messages have you your site. Many large, enterprise sites are still struggling with the cost and technology impacts of the HTTPS transition, and its impact on CDN contracts. Other sites simply struggle with mixed-content errors, and other similar limitations in the protocol. The good news is that, in addition to the ideal solution that the browsers would prefer, there are some viable alternatives, that will improve the situation until full HTTPS compliance can be achieved.
Option 1 – The Ideal Fix
The browsers’ and search engines’ push for security will continue for the foreseeable future, so the best path forward for now and for the long term is obviously to convert your entire site to HTTPS. Google Search Console specifically says in their message:
Use HTTPS pages to collect sensitive informationTo prevent the “Not Secure” notification from appearing when Chrome users visit your site, move collection of password and credit card input fields to pages served using the HTTPS protocol. Read the WebFundamentals article.
Luckily, it is getting easier to transition to HTTPS, especially with the following resources:
- Free TLS certificates
- Help deploying your certificate
- Instructions on migrating your server to HTTPS
- A checklist for migrating your website and letting Google know
- A Google help forum and Google Plus conversations if you get in you get stuck
- Firefox support if you run into issues
- Mythbusting HTTPS pitfalls
- Transparency reports and FAQs to see how the web is migrating to HTTPS
- Google rewards you with a ranking boost for HTTPS pages
Option 2 – The Short Term Fix
If your site is still in the process of transitioning to HTTPS, it might be advisable to make some minor updates so that you can minimize the impact of these new security warnings. To avoid any site-wide issues that are associated with a site-wide login capability in the page templates, move the login prompts to a single dedicated login landing page, and simply link to it from the old location of the login, in the previous templates. The dedicated login page will still receive the alert if it is not on HTTPS, but at least the alert will be limited to that page, (at least for now). Also, it is often easier to transition a subdomain to HTTPS, but leave the primary domain on HTTP, so if you have a secure subdomain on the domain, or can create one, the login page can be hosted there. If it is impossible to remove the login functionality from all of the page templates, it might be valuable to at least remove the login functionality from the top conversion pages templates, and if they are different, the top organic landing page templates.
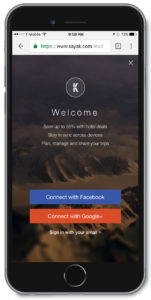 Something else you can do is try keep your users logged into the site for a longer default period of time by setting cookies. Since most page templates stop requesting that visitors login once they are logged in, this will at least minimize the impact for your most dedicated users who already have credentials, and are most-likely to actively engage with the site. Similarly, if you have a modal login popup, you can replace the login fields with social buttons to log in with Facebook, Google or LinkedIn credentials. These buttons will not trigger any warning. Then, you can include a hyper-link to the dedicated login-landing page below the social login buttons, as Kayak did, in the example on the right.
Something else you can do is try keep your users logged into the site for a longer default period of time by setting cookies. Since most page templates stop requesting that visitors login once they are logged in, this will at least minimize the impact for your most dedicated users who already have credentials, and are most-likely to actively engage with the site. Similarly, if you have a modal login popup, you can replace the login fields with social buttons to log in with Facebook, Google or LinkedIn credentials. These buttons will not trigger any warning. Then, you can include a hyper-link to the dedicated login-landing page below the social login buttons, as Kayak did, in the example on the right.
NOTE: Kayak actually does not link to a dedicated landing page here, but just brings up new information in the interstitial, which could probably still trigger the warning, but this is what the recommended implementation would look like, as long as the login hyperlink opened a new page.
Conclusion
The web is changing and webmasters must do what they can to keep with the technology. Browsers and search engines are also doing a lot to encourage adoption of the HTTPS protocol to protect users and prevent their technology from enabling privacy breaches, and identity theft. Historically, browser warnings and notifications have focused on protecting personal financial information, but now Chrome and Firefox are expanding to include warnings to inform users of risk to their basic login credentials too. While these browser updates will not have a direct impact on search engine rankings, they could have a dramatic impact on your website’s bounce rate, engagement rate, and conversion rate that in the long term could result in a secondary or indirect impact on rankings. The web was not meant to be stagnant and webmasters so SEO’s should all be preparing for these browser updates, but also advocating for the best technology available; in this case, it starts with HTTPS.
Linked Resources
- Google blog on the expected next steps in security alerts for Chrome: https://security.googleblog.com/2016/03/securing-web-together_15.html
- Post duplicated in the Chromium blog: https://blog.chromium.org/2016/09/moving-towards-more-secure-web.html
- Google article on several reasons for moving to HTTPS: https://developers.google.com/web/fundamentals/security/encrypt-in-transit/why-https
- Google’s blog detailing each Chrome release: https://chromereleases.googleblog.com/
- Information from Mozilla on how Firefox releases updates: https://support.mozilla.org/en-US/kb/update-firefox-latest-version
- Mozilla’s Firefox release calendar for 2016: https://blog.mozilla.org/futurereleases/2016/02/04/update-on-2016-firefox-release-schedule/
- Tweet breaking the secure update for Firefox 51: https://twitter.com/rlbarnes/status/814579588072349697
- Tweet confirming Firefox’ update with a visual example of saved login treatments: https://twitter.com/ryanfeeley/status/801539237682302987
- Article referencing the Firefox updates in v51: http://techdows.com/2016/09/firefox-51-insecure-password-warning.html
- Google’s Search Console: https://www.google.com/webmasters/tools/
- Download Chrome Beta: https://www.google.com/chrome/browser/beta.html
- Download Firefox Beta: https://www.mozilla.org/en-US/firefox/channel/desktop/?v=a
- Google’s help center article on making changes to avoid the new security warnings: https://developers.google.com/web/updates/2016/10/avoid-not-secure-warn
- Free automate security certificate authority from ISRG: https://letsencrypt.org/
- Automate enabling your security certificates from EFF & Let’s Encrypt on your site: https://certbot.eff.org/
- Google help workflow & checklist for moving your site to HTTPS: https://support.google.com/webmasters/answer/6033049?hl=en
- Google Webmaster Central forum – volunteers and Google employees can answer questions and help you troubleshoot migrating to HTTPS: https://productforums.google.com/forum/#!forum/webmasters
- Google Webmaster Google+ post confirming the browser warning change: https://plus.google.com/+GoogleWebmasters/posts/iDUi5pCNuLZ
- Google video on mythbusting HTTPS: https://www.youtube.com/watch?v=e6DUrH56g14
- Google blog updating their work on HTTPS and leading into their transparency report: https://security.googleblog.com/2016/03/securing-web-together_15.html
- Google’s transparency report which includes data on major sites going HTTPS: https://www.google.com/transparencyreport/https/faq/?hl=en
- Google blog confirming the use of HTTPS as a ranking signal: https://webmasters.googleblog.com/2014/08/https-as-ranking-signal.html
MobileMoxie cares a lot about security and all things mobile. Reach out and chat with Ashley or the MobileMoxie team anytime!